I bet you’re a bit like me, sometimes when I see an article I’d like to read later, I email it to myself by filling up a simple form from the article website with my email address. When you retrieve it from your inbox, you realize there is another email sent to yourself. You open it and know immediately that you didn’t send it. Yet, the email appears to come from your email address!
This is when
Email Spoofing occurs. Someone has modified the email header so the message appears to come from somewhere other than the actual source. It’s a tactic used to make people open an email because they think it has been sent by a legitimate source or someone they would recognize. It aims to get recipients to open or respond and react to that solicitation or campaign.
There are two types of Email Spoofing you could receive: The nuisance and the malicious. The former requires minimal action such as deleting. The latter can cause serious cyber liability exposures and pose security risks for your business operations and even reputation.
Construction (including the professions working in it) is the second most targeted industry for email fraud attacks. According to a recent examination (third quarter of 2018) conducted by ProofPoint on Fortune Global 500 customers,
the industry received “61 attacks per company”.
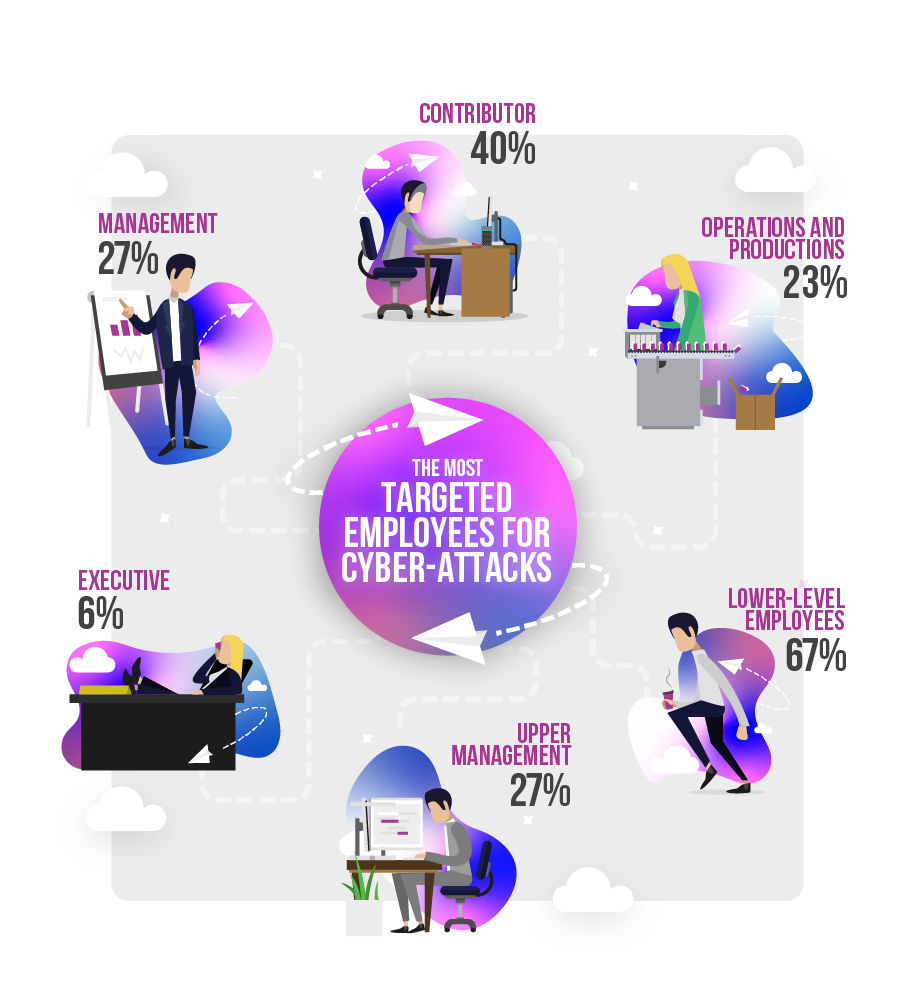 Predictably, as a group of individuals within departments ‘Lower-level employees’, such as customer service representatives, were subject to 67% of highly targeted attacks, with those in marketing, public relations and human resources accounting for nearly 20% of all phishing and malware attacks.
Predictably, as a group of individuals within departments ‘Lower-level employees’, such as customer service representatives, were subject to 67% of highly targeted attacks, with those in marketing, public relations and human resources accounting for nearly 20% of all phishing and malware attacks.
However, given that upper management accounts for a smaller proportion of businesses, it suggests that those in C-level positions, directors and department managers may be targeted disproportionately more often.
(Image courtesy Reboot Online)
The good news is, the
AIA Trust has identified
common sources of cyber liabilities and a cyber risk kit to stay ahead of the spoofing curve, malware, and phishing scams.
In addition, here are five top tips for avoiding these cyber liability exposures from
Reboot Online:
1. Know what to look for:
Pay close attention to attachments, advertisements and pop-up alerts, ensuring you only open what you trust. Train users to spot malicious emails and websites by knowing what to look out for.
2. Avoid unsolicited links and attachments:
Most commonly, you should know the sender of an email and trust the source it is coming from. If unsure, go with the assumption that it is best to avoid opening emails from an unknown source/sender altogether. And although a lot of companies employ malware scanning features, you shouldn’t be solely reliant on this.
3. Turn off email HTML:
Adding HTML can sometimes automatically run malware scripts within an email once it has been opened. For this reason, you may choose to disable it, lowering the risk of an attack.
4. Scan external drives:
Many USB and external hard-drives can hold malware and spread across the workplace onto other computers. To be extra vigilant, it is recommended that you scan all external devices with anti-virus software each time you connect an external portal to a computer.
5. Regularly change your password:
Though this may seem obvious, it is easy to forget to regularly update your passwords or be reluctant to do so in fear of forgetting them. However, for security purposes it is good practice to change your passwords every 90 days.
Just one more thing: Get educated on email headers. Message headers give valuable insight into an email’s routing history, including the sender, recipient and subject. Regardless of the email client, viewing email headers for a specific message is relatively simple. Refer to the following
AppRiver article for instructions on viewing message headers in many common clients.
So what do you do the next time you receive a message from yourself that you did not send, an email that appears to be sent by a colleague yet the content seems out of character, or an attempt to get bitcoins (and if not received some form of blackmail will be sent to each of your contacts such as family members, coworkers, etc.)?
What most people would do in any of these situations is to take these cyber exposure tips as business tools to help mitigate liability.
---
Lira Luis, AIA, NCARB, RIBA, CEM, LEED AP, principal architect at ALLL/Leapfrog Project, organized and led AIA Practice Management’s (PMKC) “Virtual Practices: The Impact of Technology and Transience on New Histories in Practice” partner program at the 2017 Chicago Architecture Biennial, subsequently co-authored a resulting white paper with AIA Trust “An Architect's Guide to Virtual Practice” that reached more than 30,000 AIA members, and moderated the webinar “Virtual Architectural Practice – An Alternate Reality”. At A’16 Conference on Architecture she shared solutions about the gig economy and potential for Virtual Practices in “Rethinking the Workplace: Co-Working Spaces for Architects”. She brings more than 25 years of architecture experience and is emeritus chair of AIA PMKC. After graduating from the Frank Lloyd Wright School of architecture, working in firms in the USA and abroad, earning NCARB certification, she now runs a hybrid traditional and virtual practice.